

We Are All Under Attack
Hackers command and control distribution networks known as “bot-nets”, which are compromised servers & devices mainly in Russia, China, Southeast Asia and other hacker-friendly countries around the globe. These bot-nets are also known as “Zombie Armies” and are used to send DDoS attacks, spam or phishing emails, extort money, steal identities, infect other servers and workstations, or just bring down a website or network for their own agenda.
Below is a Live Map of cyberattacks in real-time.
Our subscribers are blocking over 99% of these attacks.

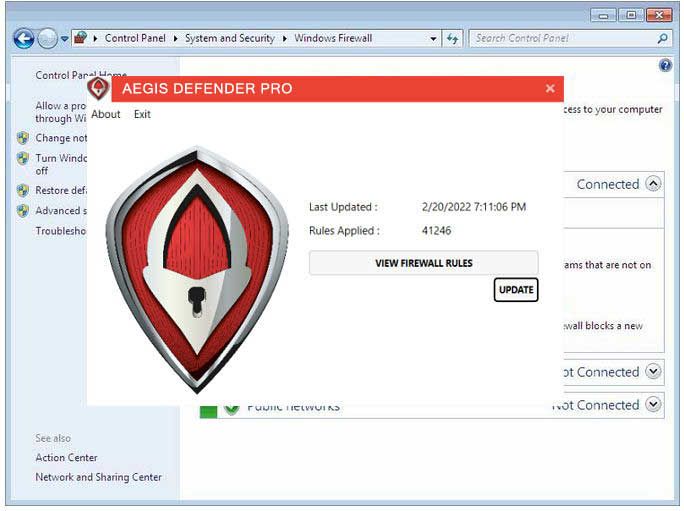
Aegis Defender Pro for
Windows Server and PC
Aegis Defender Pro works by updating the native firewall of Windows with thousands of consolidated Rules to block 770 million IPs used by hackers, spammers, Ransomware servers and botnets from your server, PC or laptop.
Each of these entries are researched & verified in real-time, as attack reports are received by our specialists. Once verified, they are added to our Master Blocklist, which is downloaded and applied to your Firewall automatically every hour.
When one client is attacked, all become protected from that attacker within minutes.
Endpoint Protection
For Windows Server, PC & Linux
Stay one step ahead of potential attacks.
Endpoint Firewalls are updated with new entries 24/7/365, ensuring that all servers and workstations are fully synchronized and protected. Our real-time attack detection and hourly firewall updates enable us to identify and block threats before they reach your systems.

The First Automated Firewall Updating Service
Since 2016, we have collected and researched over 770 million IP addresses used for cyber-attacks on clients, abuse databases, and Government sources, originating from both overseas and the USA.
Detection
Detection and identification of cyber-attacks on our clients email, websites and servers with third-party security systems.
Research
Each reported IP Address is researched for abuse, traced to it's point of origin and the network it is from.
Update
The IP Address or entire CIDR is added to our Master Blocklist and syndicated to every client within minutes.
Case Study - "Server E1"
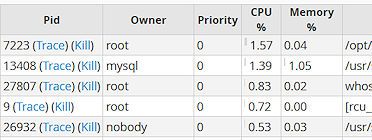
Prior to implementing Aegis Defender Pro on Server E1, the server was frequently targeted by cyber attackers who used techniques such as SQL injections, thousands of fake logins, session poisoning, and DFI attacks to disrupt its operations. The server was severely impacted by these daily attacks, resulting in significant CPU and memory usage, crashing the server at peak times.
After installing Aegis Defender Pro, the server's CPU usage decreased from 95% to 11%, while memory and available bandwidth increased dramatically. The server has not slowed or crashed in over 4 years since.
Over 90,000 Attacks a Day
Every day, tens of thousands of IPs are attacking every server and device they can find online.
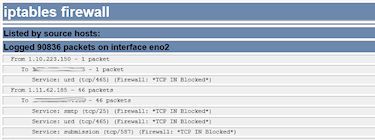
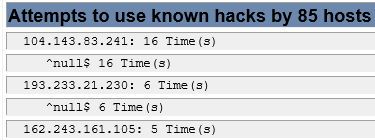
Less Than 1% Penetration
Out of 90,000 attempts, 85 penetrated the firewall and were blocked at the server level.
Performance Boost
When you remove all attacks on a server, all resources can be dedicated to real operations.
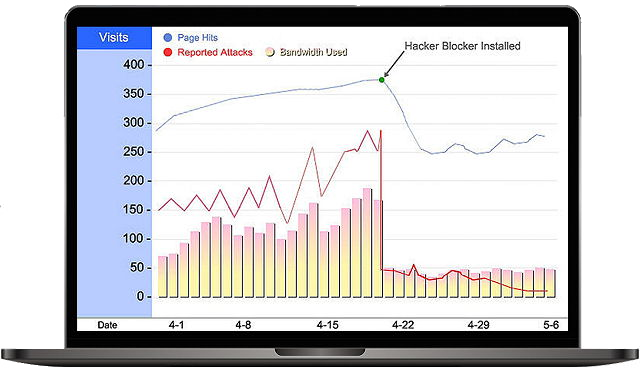
Server Performance Boost, More Available Bandwidth
Public-facing servers suffer a barrage of attacks every minute of every day. Aegis Defender Pro stops many of these attacks instantly.
- Faster Servers & Network
- More Available Bandwidth
- Drastic Reduction in Attacks
The Master Blocklist
Our Master Blocklist is the culmination of years of work from thousands of sources around the world. Combining databases from abuse reporting websites, Government sources and cyber-attacks on our own clients, we've created one of the most comprehensive lists of IP addresses and CIDRs used by C2 Commanders, Bot-Nets, Spammers, Hackers and Malware and Ransomware-as-a-Service (RaaS) servers.
Most blocked IPs are compromised web hosting servers and IoT devices. We take great care in our IP blocks, to ensure legitimate traffic is unaffected.

Complete Protection Made Easy
Fully Managed Firewall Updates 24/7/365